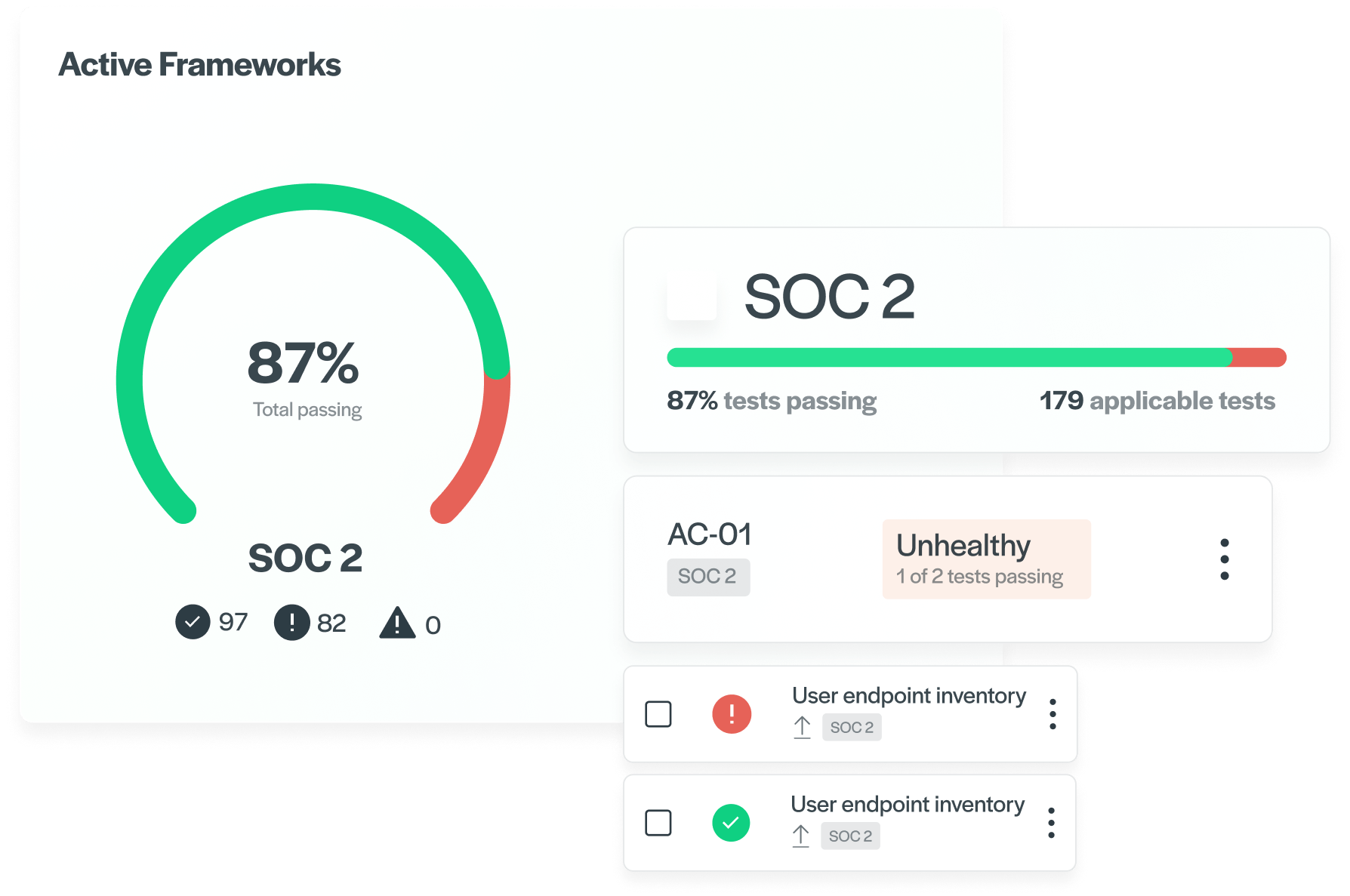
Software-as-a-Service (SaaS) companies are those that offer tech products and services over the Internet. Over the last decade, SaaS companies have become popular as there are no downloads or installations required and users can simply create an online account and log in to access products and services. At the same time, this SaaS model puts greater pressure on the companies because they must have high levels of security to protect customer data. More importantly, they must showcase that they are taking the right steps to protect data security and privacy.
This is where SOC 2 compliance helps. System and Organization Controls 2 (SOC 2) is a comprehensive framework created by the American Institute of Certified Public Accountants (AICPA) to evaluate the security posture of an organization. It is a continuous monitoring framework that assesses whether an organization has the necessary controls, policies, and processes to protect data.
Why is SOC 2 Compliance Important for SaaS Companies?
SOC 2 compliance is particularly important for SaaS companies because they handle confidential customer data like credit card numbers, date of births, and sometimes even an organization’s confidential data. Also, users interact with these tools through the Internet, where even the smallest of mistakes can lead to major data breaches.
Though SOC 2 is a voluntary compliance framework, many organizations comply with it because it improves their security and more importantly, creates trust in the minds of users, investors, and other stakeholders. Also, this compliance can prove to be a market advantage in a competitive business environment. Additionally, the SOC 2 framework identifies risks early, so organizations can mitigate them before they impact the organization.
Due to these reasons, SOC 2 is an essential regulatory framework for SaaS companies.
How to Achieve SOC 2 Compliance?
Achieving SOC 2 compliance requires a planned and coordinated approach. Below are the broad steps involved in achieving compliance.
Step 1: Preparation
As a first step, identify the goals and reasons for compliance. It can be to improve security, gain a better reputation, and more. Based on these goals, decide if you want to go with SOC 2 Type I or Type II certification. A key difference is that Type I evaluates the effectiveness of controls at a specific point in time, while Type II evaluates the same over a specified period. Also, create a compliance team and provide the necessary training to get started.
Step 2: Gap Analysis
Do a Strengths, Weaknesses, Opportunities, and Threats (SWOT) analysis to help understand the gaps in your operations. Evaluate these gaps against goals, and accordingly, devise an action plan to bridge them.
Step 3: Implementation of Security Controls
Understand the five security principles of SOC 2 compliance framework and based on your operations and goals, devise the appropriate controls, like:
- Access controls to limit access to sensitive data and systems.
- Encryption to protect data at rest and during transit.
- Real-time tracking of security events.
- Incident response plan in the event of breaches or system failures.
- Disaster recovery for business continuity.
Step 4: Policies and Procedures
Support the security controls with appropriate policies and procedures. For example, set role-based access based on your access controls. Document these policies and make them accessible to all employees. Continuously review and update them as needed.
Step 5: Continuous Monitoring and Audits
Now that the policies and procedures are established, set up a system to continuously monitor their implementation. Conduct internal audits as needed to check if everyone is following the established policies. Consider using tech platforms to automate this tracking. In case of gaps, identify and remediate them at the earliest.
Step 6: Audits by External Auditors
To get SOC 2 certification, your controls, and their implementation must be audited by a qualified external auditor. Prepare for these audits by getting the right documentation. Centralize the required information and streamline access to this content, so the auditors can quickly find what they want. At the end of the audit, these auditors will provide feedback. Make sure to implement them.
Step 7: Maintain Compliance
Strive to continue these policies and their implementation to maintain compliance with SOC 2. Periodically conduct internal audits and review these policies. Based on your changing requirements, make sure to update them.
With these steps, you can achieve SOC 2 compliance.
Challenges in SOC 2 Compliance for SaaS Companies
SOC 2 Compliance is not always easy, as it requires extensive preparation and documentation. Here are a few challenges that SaaS companies may face in getting SOC 2 compliance.
- Compliance audits and subscriptions to compliance tracking tools can be expensive.
- If you have many security controls, monitoring, and documentation can get complex.
- Achieving SOC 2 compliance, especially Type II, can be time-consuming.
- Getting all the employees to follow security policies will not be easy.
- SaaS companies tend to rely on third-party providers, and getting them to become SOC 2-compliant can be challenging.
Despite these challenges, many SaaS companies are taking the effort to achieve SOC 2 compliance because of its many benefits for their operations and reputation.
Best Practices for SOC 2 Compliance
Addressing the above-mentioned challenges and improving compliance requires a concerted approach. Below are some best practices that come in handy.
- Plan ahead, so you can achieve compliance within the required timeframe.
- Use automation tools to track your security controls. This can save a ton of time and effort.
- Train employees and create a security-first culture within your organization.
- Regularly review your security policies and ensure they are relevant to your operations.
- Keep an eye out on the security posture of your vendors.
- Regularly conduct penetration testing and vulnerability assessments.
With these best practices, you can achieve SOC 2 compliance.
Top 5 Tools for Automating SOC 2 Compliance Processes
Vanta
Vanta is one of the most popular compliance automation platforms available today. Its trust management platform automates many tasks, saving time and effort. Moreover, it can be used to achieve compliance with other standards like ISO 27001, GDPR, and HIPAA.
Source: Vanta
Key Features
- Automated evidence collection and monitoring.
- Pre-built templates for policies and controls.
- Integration with cloud services and SaaS tools.
- Real-time alerts for security vulnerabilities.
- Audit preparation and reporting.
Overall, Vanta simplifies the compliance process by automating repetitive tasks, reducing manual effort, and providing a centralized platform for managing compliance.
Drata
Drata automates the complete SOC 2 lifecycle to save time and resources. Also, it offers continuous monitoring and is highly scalable to meet your organization’s needs. It can be extended to other frameworks as well.
Source: Drata
Key Features
- Continuous monitoring of security controls.
- Automated evidence collection and audit readiness.
- Customizable control frameworks.
- Employee training and policy management.
- Integration with over 75 tools (e.g., Jira, Okta, AWS).
Drata’s focus on continuous compliance and real-time auditing helps SaaS companies maintain their compliance posture always, not just during audits.
Secureframe
Secureframe is another popular SOC 2 compliance platform that automates and streamlines the process. A highlight is that it condenses 200+ controls into eight easy steps to move ahead quickly with SOC 2 compliance.
Source: Secureframe
Key Features
- Helps companies become SOC 2-compliant in weeks.
- Automates vendor risk management and security policy enforcement.
- Provides an easy-to-use compliance dashboard for audit readiness.
- Offers pre-built policies and procedures.
- Supports employee training and phishing simulations.
Secureframe’s user-friendly interface and comprehensive feature set make it easy for SaaS companies to manage compliance with limited resources.
OneTrust
OneTrust is a good choice for SaaS companies that need to manage privacy regulations and broader GRC requirements along with SOC 2. Its ability to integrate privacy and security efforts makes it a powerful tool for organizations with complex compliance needs.
Source: OneTrust
Key Features
- Automates evidence collection, control monitoring, and audit readiness.
- Provides pre-built templates for SOC 2-compliant policies, procedures, and controls.
- Identifies and mitigates risks through integrated risk management tools.
- Connects with cloud providers, SaaS tools, and other OneTrust modules for a unified approach.
In all, OneTrust is a comprehensive GRC platform for managing risk, implementing the security controls of SOC 2 and other compliance standards, and monitoring vendor compliance.
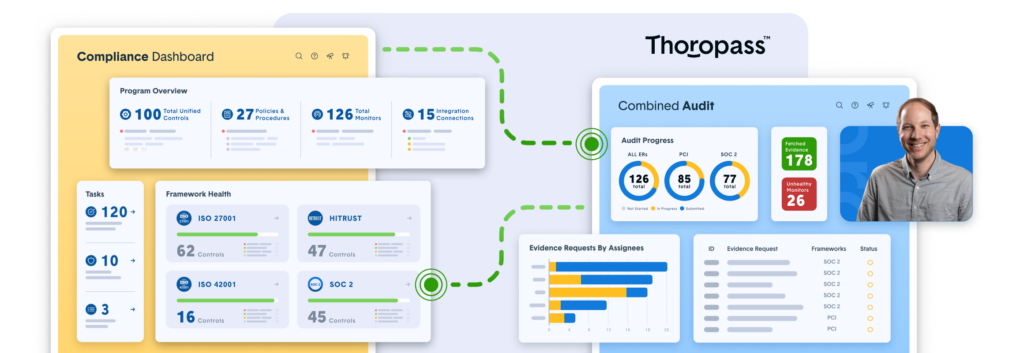
Thoropass
Thoropass is an audit and automation compliance platform that helps with SOC 2 audits. A highlight of this tool is its expert guidance, which offers a hands-on approach to help SaaS companies navigate the complexities of SOC 2 compliance.
Source: Thoropass
Key Features
- Combines automation with human expertise for a guided compliance process.
- Offers real-time monitoring of security controls and risk assessments.
- Connects businesses with in-house auditors for a seamless audit process.
- Supports multiple frameworks, including SOC 2, ISO 27001, HIPAA, and GDPR.
Overall, Thoropass’s human touch to an automated process is its highlight, and this is where it can help startups and other SaaS companies that are new to SOC 2 audits.
Final Thoughts
To conclude, SOC 2 compliance is important for SaaS companies to boost their security and to maintain their credibility. However, achieving this compliance can be challenging, especially if you are starting out. We hope the information presented in this post provides the guidance you need to kickstart your compliance.