Rapid advancements in technology, including AI, have increased the rate of cybercrime as well because the entry barriers have greatly dropped. Also, the emergence of ransomware-as-a-service has further increased the number of cybercrimes, as more people and groups can attack organizations with few resources. All these developments have a big impact on organizations, as they strive to use various tools and strategies to counter these attacks and to continue to comply with regulations like GDPR, AML, and HIPAA.
In particular, financial organizations are finding it increasingly difficult to meet the requirements of AML, and this is where it helps to have tools like ComplyAdvantage, as they can automate many required processes and combine them with continuous monitoring.
However, ComplyAdvantage may not work for all organizations, and this is why this guide explores the alternative tools and how they fare in comparison with ComplyAdvantage.
A Brief Look Into ComplyAdvantage
ComplyAdvantage is an AI-driven AML fraud and risk detection software. This SaaS tool taps into global intelligence to safeguard your business from fraudulent customers and those in the Politically Exposed Persons (PEP) and other watch lists. One of the highlights of this tool is its real-time monitoring of customers and transactions to provide the insights you need to immediately tackle fraud. Its audit trails, reports, and API integrations are other notable features.
That said, ComplyAdvantage also comes with many downsides. Many online user reviews show the following issues.
- A high number of false positives.
- Inconsistent alert notifications.
- Over-reliance on AI
- Limited customization.
If you’re grappling with one or more of these downsides, below are a few alternatives to consider.
1. Dow Jones Risk & Compliance
Dow Jones is a business intelligence tool that analyzes global databases and offers data sets for sanctions, watch lists, PEPs, and adverse media. It is a preferred choice for banks and financial institutions that demand trustworthy, regulator-recognized data. It also provides information about bribery and corruption risks, along with an effective due diligence program for meeting compliance requirements.
Source: Dow Jones
Why it’s a Good Alternative
Dow Jones is one of the leaders in the AML compliance space, as it taps into reliable and extensive data from premier global databases. Its tools integrate with common KYC/AML platforms and are used by global banks and insurers. The platform’s reliability and accuracy make it a preferred vendor for many top organizations in the world.
Key Features
- Sanctions, PEP, and watch list data from over 200 countries.
- Editorially curated adverse media from premium sources.
- Batch and real-time screening.
- Flexible integration with case management tools.
Pros:
- Trusted by global regulators.
- High data quality and low false positives.
- Extensive adverse media archives.
- Customizable screening workflows.
Cons:
- Expensive for smaller firms.
2. LSEG World-Check
Part of the London Stock Exchange Group, World-Check is a pioneer in the risk intelligence industry. Its dataset is one of the most comprehensive in the industry. It also structures the data in a way that helps meet your AML and third-party due diligence checks.
Source: LSEG
Why it’s a Good Alternative
World-Check provides deep sanctions, watch lists, and PEP data, used by over 10,000 organizations globally. Its breadth of coverage, historical archiving, and regulator acceptance make it ideal for institutions under constant audit pressure. This platform also integrates well with CRMs and transaction monitoring systems.
Key Features
- Global PEP and sanctions coverage.
- Adverse media monitoring.
- Ongoing due diligence and monitoring.
- Easy export for audit compliance.
Pros:
- High trust level among regulators.
- Reliable historical data.
- Well-established industry presence.
- Suitable for global operations.
Cons:
- Higher false positive rates.
3. LexisNexis Risk Solutions
LexisNexis is a global data and analytics company offering AML compliance, fraud detection, and identity verification in a single package. It enables organizations to manage AML compliance challenges across the entire lifecycle of customers. More importantly, it provides detailed visibility into all your critical workflows.
Source: LexisNexis
Why It’s a Good Alternative
LexisNexis links data across billions of public records using unique entity resolution technology. It’s especially effective for layered compliance involving both identity verification and risk scoring. Integration support is strong, with SDKs and REST APIs for seamless onboarding.
Key Features
- Identity and document verification.
- AML watch list and PEP screening.
- Device, geolocation, and IP analysis.
- Risk scoring and fraud detection.
Pros:
- Multi-layered AML and fraud prevention.
- Robust analytics capabilities.
- Longstanding legal credibility.
- Scalable for global organizations.
Cons:
- It can be complex to configure.
Contact the sales team for more details.
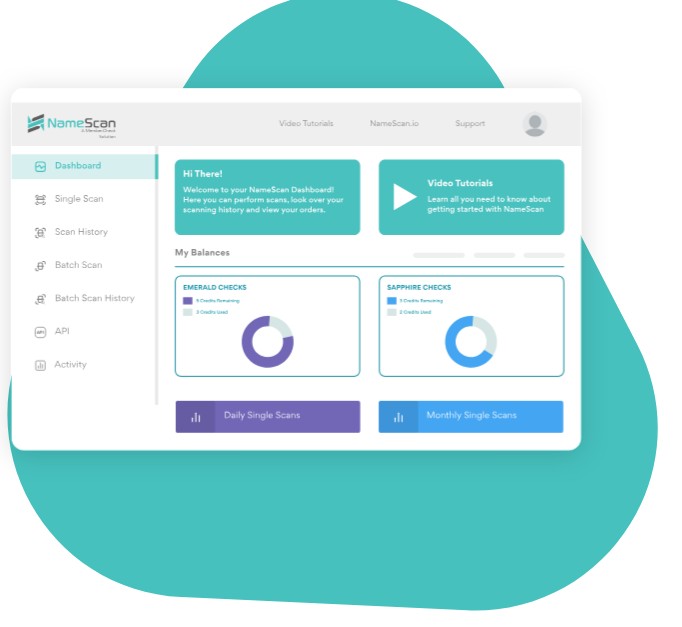
4. NameScan
NameScan is a free PEP and sanctions check tool that works well for simple KYC and AML workflows. Its paid version offers AML/CTF screening tools with real-time access to updated global datasets. Also, it is highly affordable, making it more suitable for startups and SMEs looking for affordable compliance solutions.
Source: NameScan
Why It’s a Good Alternative
NameScan is ideal for small firms that need quick compliance deployment without heavy integration. It supports both manual and batch screening and allows businesses to scale up without licensing headaches. Its affordability and flexibility make it a common choice for boutique financial service firms.
Key Features
- Access to Dow Jones and other global watch lists.
- Real-time PEP and sanctions screening.
- On-demand and batch scanning.
- Plug-and-play SaaS interface.
Pros:
- Low-cost entry for small firms.
- No long-term contracts.
- API and manual options.
- Simple and clean UI.
Cons:
- Limited advanced analytics.
- Not suitable for high-risk or high-volume screening.
5. GBG
GBG is a global leader in identity verification, AML screening, and fraud prevention. Serving over 20,000 clients in more than 70 countries, GBG combines advanced technology with local data sources to help organizations onboard customers, manage risk, and stay compliant. It is also user-friendly and makes onboarding for customers as well.
Source: GBG
Why It’s a Good Alternative
GBG offers a wide suite of tools that go beyond basic AML checks. With its Identity Data Intelligence platform, organizations can verify identities in real-time, screen against global sanctions lists, and assess fraud risk through a single API. Its localized data partnerships give it an edge in verifying customers in hard-to-reach or high-risk jurisdictions. GBG’s modular structure also allows businesses to customize their compliance based on their requirements.
Key Features
- Identity verification across 70+ countries.
- Global sanctions, PEP, and watch list screening.
- Document verification and biometric authentication.
- Fraud detection, device intelligence, and geolocation analysis.
Pros:
- Strong global coverage, including difficult markets.
- Easy integration with a modular setup.
- Combines AML, fraud prevention, and identity proofing.
- Scalable for both startups and enterprise use.
Cons:
- Some advanced features require technical setup.
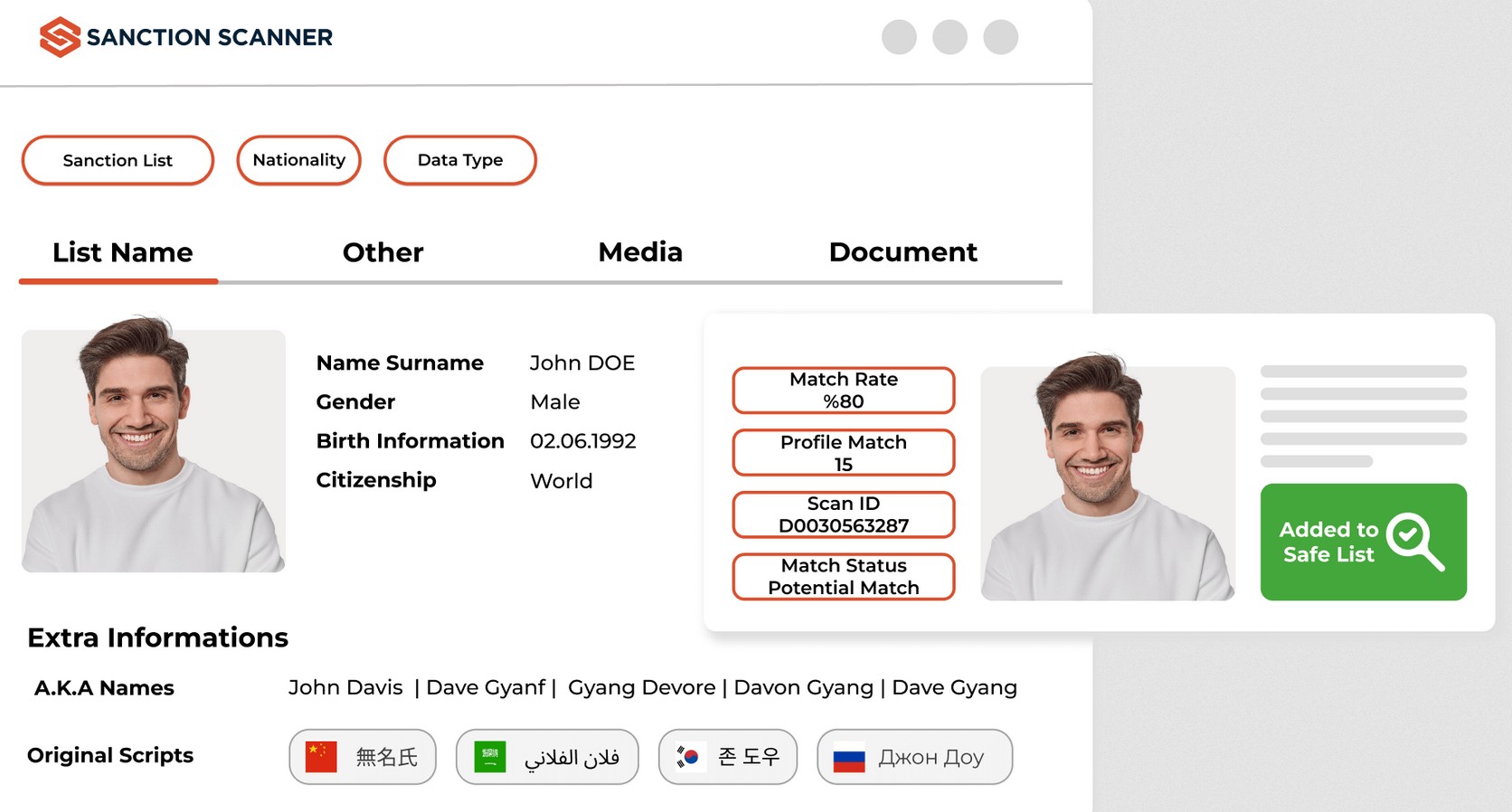
6. Sanction Scanner
Sanction Scanner is another popular AML solution designed for fast-growing fintech and cross-border platforms. It scans customers across 3000+ global sanctions, PEPs, and watch lists and monitors every transaction in real-time. It even assigns risk scores to customers based on their profession, age, income, country, and currency to provide better control and visibility into risky customers and transactions.
Source: Sanction Scanner
Why It’s a Good Alternative
Sanction Scanner provides real-time screening from more than 200 government lists, in addition to data from other watch and sanction lists. It is highly flexible and simple to use for non-technical users. Its well-developed APIs make it easy for organizations to integrate Sanction Scanner into their existing workflows.
Key Features
- Over 3000+ sanctions and PEP lists.
- Real-time and batch screening.
- Adverse media and ongoing monitoring.
- Developer-friendly documentation.
Pros:
- Startup-friendly pricing.
- Transparent audit logs.
- Simple UI for compliance teams.
- High-frequency list updates.
Cons:
- Less recognized by regulators.
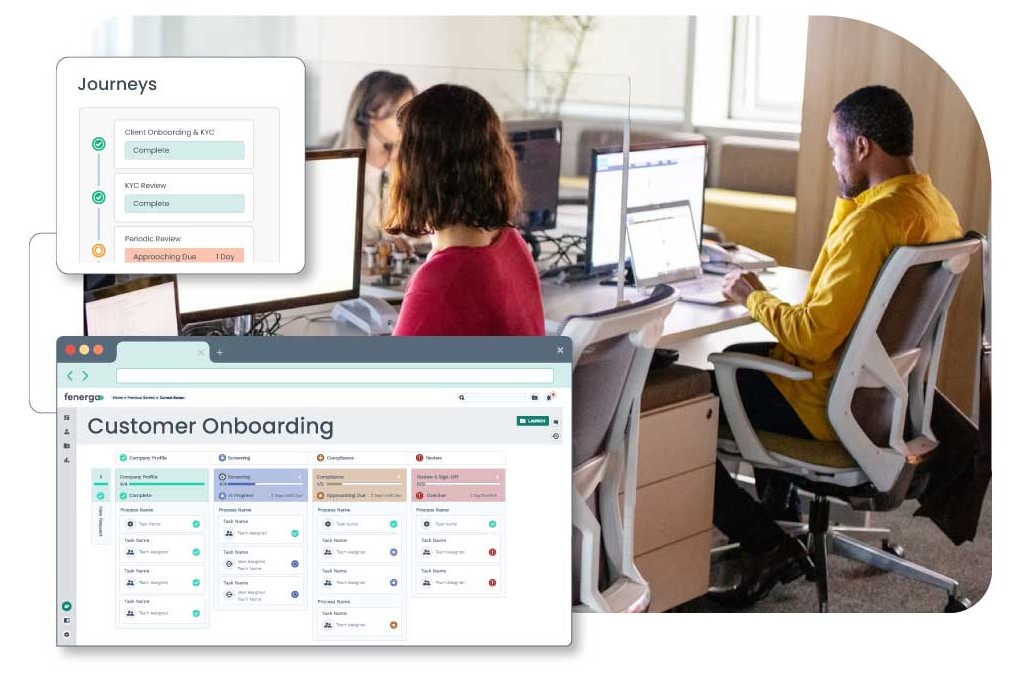
7. Fenergo
Fenergo is a financial compliance and client lifecycle management platform that integrates AML, KYC, onboarding, and regulatory reporting capabilities into a single platform. It automates the document management process, improves operational efficiency, and reduces operating costs.
Source: Fenergo
Why It’s a Good Alternative
Fenergo provides an enterprise-wide compliance framework that’s particularly well-suited for global organizations. It links client onboarding to AML and KYC risk profiles, which reduces friction at the time of onboarding. At the same time, it satisfies the complex regulatory requirements of most jurisdictions. It can be helpful for institutions with layered entity structures or multi-jurisdictional exposure.
Key Features
- KYC and AML rule engines.
- Regulatory reporting modules.
- Centralized risk scoring and profiling.
- Integrates with CRMs and data vendors.
Pros:
- All-in-one onboarding to compliance.
- Strong for multi-entity due diligence.
- Widely used by Tier 1 banks.
- Reduces manual work through automation.
Cons:
- Too heavy for startups or SMBs.
8. Napier
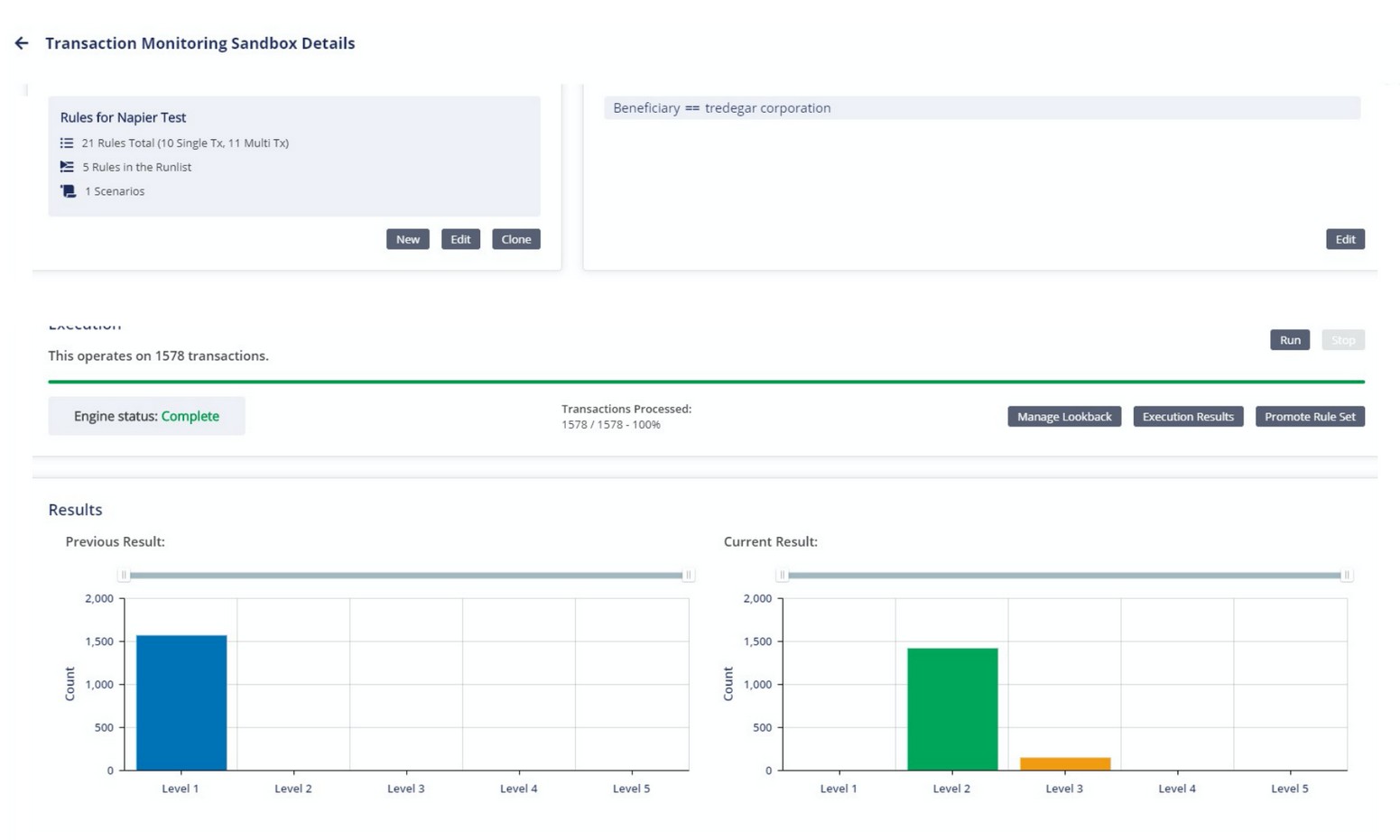
Napier is an end-to-end intelligent compliance platform that uses AI-driven tools for AML transaction monitoring, screening, and client risk assessments. This platform is known for its speed, scalability, and flexible configurations, making it ideal for organizations across all sectors. It is also known to reduce false positives and negatives, thereby enabling organizations to make decisions based on facts. A highlight of this tool is that it’s built on 100+ AML typologies to cover every kind of transaction. It also comes with a sandbox that can be used for testing rules before deploying them.
Source: Napier
Why It’s a Good Alternative
Napier’s platform is built to reduce false positives through intelligent alerting and configurable scenarios. It provides a sandbox environment for compliance teams to test and tune rules without interrupting production systems. Its AI features include explainable logic that can be further customized for different scenarios.
Key Features
- AI/ML-driven alert reduction.
- Customizable transaction monitoring.
- Case management and investigation tools.
- Real-time screening engine.
Pros:
- Explainable AI for audit transparency.
- Reduces alert fatigue.
- Strong customer support.
- Regulatory-grade documentation.
Cons:
- Complex setup for smaller teams.
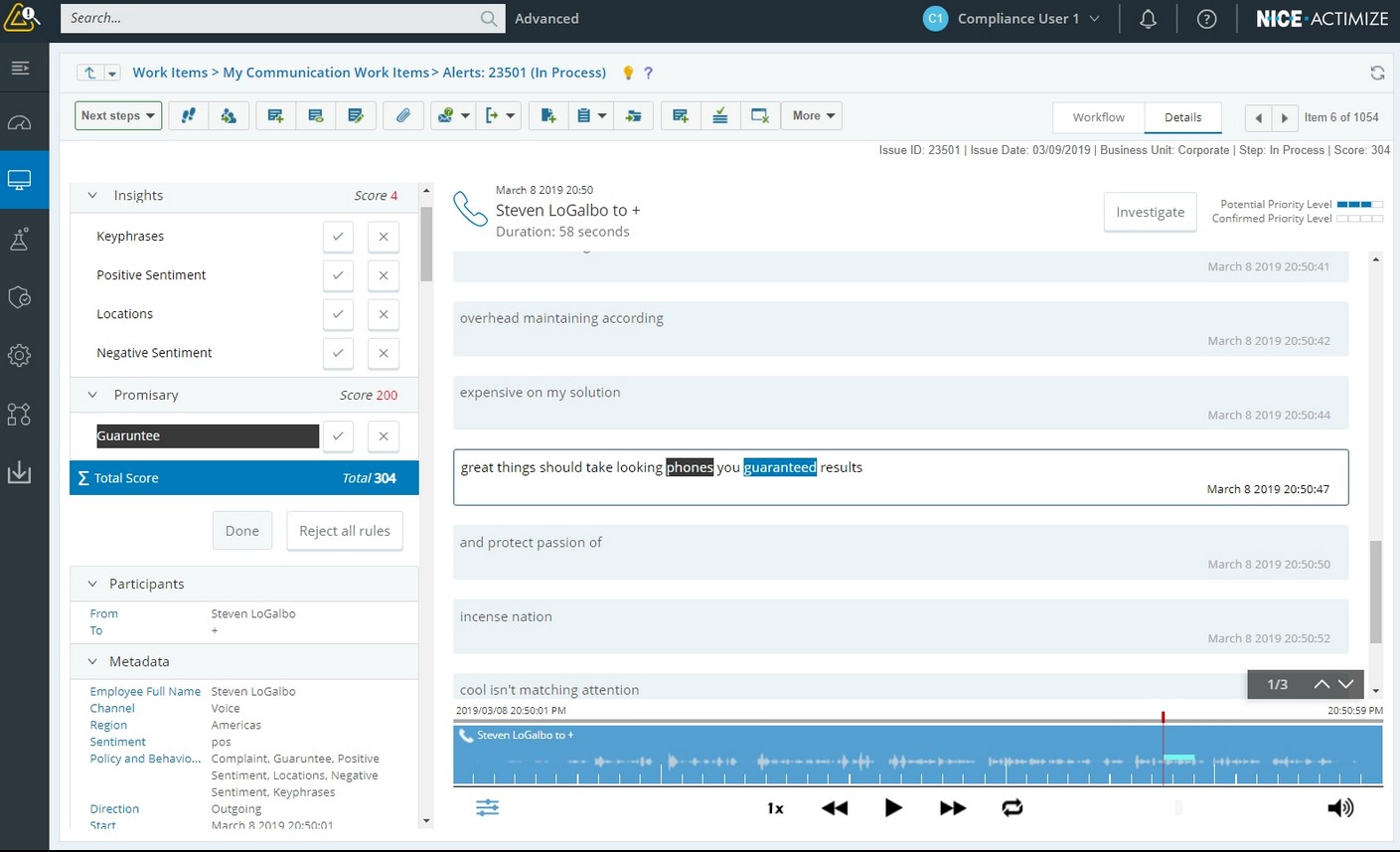
9. Actimize by NICE
NICE Actimize is a global leader in financial crime and compliance solutions, as it analyzes a wide range of data sources to identify customers and their associated risks throughout their lifecycle. It also leverages AI and machine learning to improve accuracy and efficiency while supporting audits and compliance requirements across different countries.
Source: NICE
Why It’s a Good Alternative
Actimize is a good choice for global banks handling billions in transactions, as it combines transaction monitoring, market surveillance, and customer risk scoring in a single solution. It’s also highly respected by regulators, making it suitable for institutions under intense scrutiny.
Key Features
- Advanced transaction monitoring.
- Sanctions and watch list screening.
- Market abuse detection.
- Regulatory reporting.
Pros:
- Scalable for global operations.
- Trusted by regulators.
- Full compliance ecosystem.
- Flexible, modular deployment.
Cons:
- Complex to implement and maintain.
Each of the above tools has unique features that make them better suited for some scenarios and organizations over others. Evaluate a tool’s features and their fit for your requirements before making a decision.
Final Thoughts
To conclude, AML has become an important process in today’s world, where financial crimes are becoming more widespread. Given the complexity of AML, you need appropriate tools for compliance. ComplyAdvantage is a strong AML solution that can resolve many compliance challenges. However, it’s not always the best fit for every organization. From large-scale platforms like LexisNexis and Dow Jones to flexible, startup-friendly tools like Sanction Scanner and NameScan, there’s a broad mix of alternatives available to choose from.
Each tool has its strengths, ranging from deeper data coverage, more transparent audit trails, AI-driven alert scoring, lower costs, and more. The best AML partner is the one that fits your compliance needs today while also scaling for tomorrow.