File sharing is essential to an organization’s operations, as employees have to share data with internal and external stakeholders for collaboration and decision-making. A study by Varonis shows that on average organizations share files with more than 800 domains.
However, the files may contain sensitive data and hence, cannot be intercepted or accessed by unauthorized users during transit. This is where file transfer software is essential, as it comes with features like encryption, secure transfer, and more to ensure that the data is received only by the intended recipients.
The best secure file transfer software from a compliance standpoint are:
- Kiteworks A Private Content Network (PCN) that consolidates and tracks all file transfer activities to ensure they comply with existing industry standards and best practices.
- Citrix ShareFile A managed file transfer platform for securely sending, storing, and sharing files with authorized users.
- Tresorit An end-to-end collaboration platform that uses encryption and other techniques to protect your data, from creation to sharing.
- NordLocker A secure file-sharing platform that keeps your files safe while controlling who can access them.
- IBM Sterling Secure File Transfer A scalable platform to share and track sensitive data.
Read on as we talk about secure file transfer, the protocols used, how it works, and the essential features to look for in a secure file transfer software. Finally, we also review the best tools that can secure file transfers while helping you meet data security and privacy regulations.
What is Secure File Transfer?
Secure file transfer is the process of sharing files through a secure and reliable delivery method. These methods use a combination of security features like encryption and access controls to ensure that the data is protected during transit. Moreover, these measures also help organizations comply with governance policies and industry regulations.
How Secure File Transfers Work?
To safely transfer a file from source to destination, a combination of protocols and methodologies are used. The fundamental aspect that ensures safe delivery is the underlying protocol. In the computer world, protocols are a way to standardize communication between the sender and the receiver. In this case, you’d want the sender and receiver to speak the same language for secure communication.
But, a secure protocol alone is not enough, and this is why other methods like encryption, authentication, and access controls are also implemented along with the protocol to ensure secure delivery. Sometimes, digital signatures are also used to verify the integrity and authenticity of a file.
You can imagine the protocol as the base and the other technologies as additional security layers. Given this importance, let’s look at the different protocols available today.
Secure File Transfer Protocols
Many secure file transfer protocols are commonly used, and here’s a brief look at each of them.
SSH File Transfer Protocol (SFTP)
File Transfer Protocol (FTP) is the original protocol developed for file sharing. It uses a client-server model for communication. However, it was not a secure protocol, and hence, developers added a security layer by using Secure Shell (SSH) for encryption. This resulted in the SSH File Transfer Protocol, or SFTP for short. It was created by the Internet Engineering Task Force (IETF) and is the most common file protocol used today.
Much of its popularity is because SFTP provides secure file access and transfer over a reliable data stream. Moreover, SFTP encrypts both the communication commands and the data that’s being transferred, thereby reducing the chances of eavesdropping and data theft.
FTP over SSL/TLS (FTPS)
FTPS is another secure version of FTP, where the security protection comes from Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption. Essentially, this protocol encrypts the control and data channels separately to protect against both interception and tampering.
Moreover, FTPS supports different authentication methods, like username/password, client certificates, and server-side certificates.
Hypertext Transfer Protocol Secure (HTTPS)
HTTPS is an extension of HTTP that uses SSL/TLS encryption to secure communication between clients and servers. Though this protocol is mainly used for web browsing, HTTPS can also be used for secure file transfers because it encrypts data in transit. As a result, you can reduce the chances of man-in-the-middle interceptions and tampering.
Applicability Statement 2 (AS2)
AS2 is another protocol used for sending secure and reliable data, and it uses digital certificates and Message Disposition Notification (MDN) to ensure data confidentiality, integrity, and authenticity. With this protocol, senders can get receipts for non-repudiation, which provides proof of data integrity and security. This MDN can be helpful in legal proceedings as it proves that the sender transmitted a secure file. Due to these features, AS2 is mostly used in Electronic Data Interchange (EDI) and B2B transactions.
Secure Copy Protocol (SCP)
SCP is another popular secure file transfer protocol that uses SSH for authentication and encryption. It provides a secure way to copy files between hosts on a network. Also, SCP encrypts data during transmission and verifies the integrity of transferred files. Both these features make SCP a good choice for file transfers.
ODETTE File Transfer Protocol 2 (OFTP2)
This is a TCP/IP protocol used mostly by automotive companies based in Europe. Like AS2, it also supports non-repudiation of receipts, which can make it an efficient option for transferring large files containing secure data.
User Datagram Protocol (UDP)
UDP is a file transfer protocol that’s similar to TCP/IP, but it doesn’t include mechanisms like handshakes and certificates. As a result, this is one of the fastest protocols for sending files, but not always the most secure.
Thus, these are some common protocols for securely sending data files across your organization. More importantly, they also help you stay compliant with regulations like GDPR, HIPAA, SOX, PCI-DSS, and FISMA.
Next, let’s look at some of the best secure file transfer software that can safeguard your organization’s sensitive data while helping you stay compliant with regulations.
Our Methodology
At Planet Compliance, we analyzed many tools to come up with the above list. Here are the criteria we used for evaluation:
- The use of unified security methodologies like multi-factor authentication, advanced threat protection, data loss prevention, and more.
- Focus on compliance with standards.
- Centralized dashboards for tracking file activities.
- Availability of logging and audit trail features.
Best Secure File Transfer Software
Let’s see how our selected tools fare against these criteria.
1. Kiteworks
Kiteworks is a dedicated tool that ensures privacy and security in internal and external communications. This platform is authorized by FedRAMP and is well-suited for secure file sharing, managed file transfers, and email communications. It also meets the requirements of standards like HIPAA, NIS 2, IRAP, ITAR, GDPR, CMMC, and more.
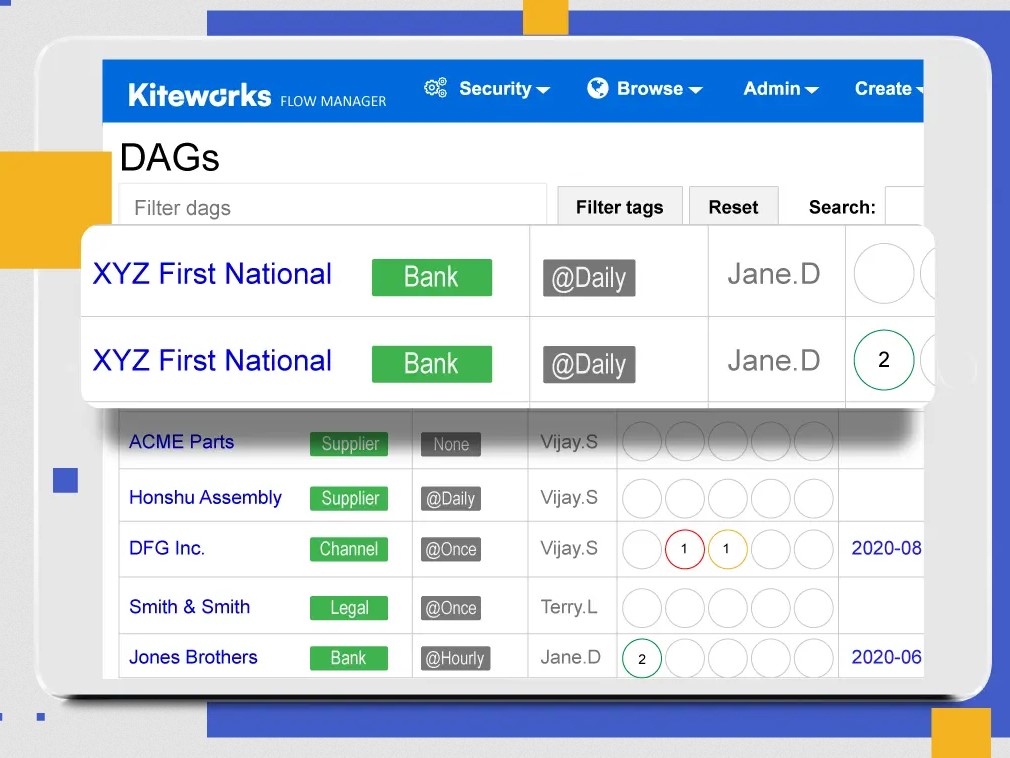
Source: Kiteworks
Here are Kiteworks’ important features.
Comprehensive Security
One of the reasons for Kiteworks to have such wide-ranging compliance is the many security features included in its offerings. It encrypts data at rest with AES-256 and data in transit with TLS 1.2 respectively. Additionally, it uses multi-factor authentication and access-based controls to streamline access to sensitive data and avoid unauthorized access. The use of advanced threat protection and data loss prevention add additional security to the shared file.
Granular Control
With Kiteworks, you have complete control over file shares. You can easily apply granular policies to control how files are shared with internal and external users. Moreover, you can decide how the files and their data must be stored and handled. All these activities are also logged for future analysis.
Dashboard
Kiteworks offers well-designed dashboards that act as a centralized place to monitor, track, and audit all activities related to file sharing. You can get real-time and historical views, and even drill down further to get the actionable details. Using this dashboard, you can get information like the timestamps for file access, IP addresses used, users who have accessed a file, and more.
Due to these features, Kiteworks can be a handy tool to securely share files while maintaining compliance.
Pros:
- Integrates well with leading cloud storage including Dropbox.
- Online backups.
- Well-designed web UI.
- Highly scalable.
Cons:
- Many users have reported bugs in the email server and its consequent delivery timelines.
- It does not support using images as digital signatures.
2. Citrix ShareFile
Citrix ShareFile is an extensive file storage and sharing platform that protects the security and integrity of your files and the sensitive information they contain. You can even use its feature called the Virtual Data Room to store sensitive files like merger and acquisition documents, audits, valuations, agreements, and more.
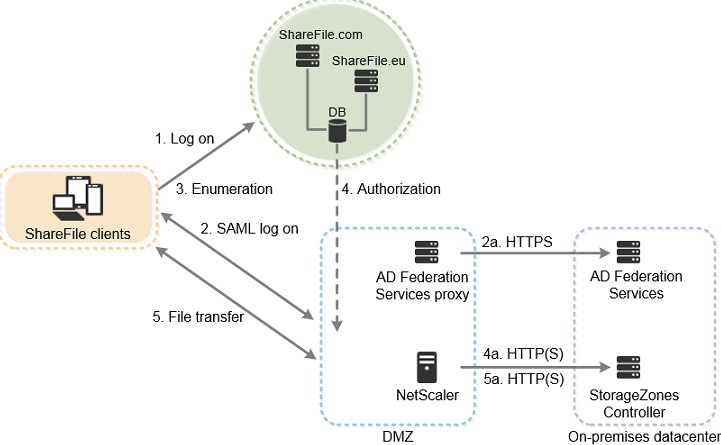
Source: ShareFile
Below are ShareFile’s notable features.
Security Notifications
ShareFile sends email notifications to alert users of security violations. You can even route the emails to specific email addresses or teams for quick and effective responses. Moreover, you can also know what notification types must be sent to different accounts. Such granular control over notifications ensures quick remediation.
Sharing and Collaboration
With ShareFile, you can securely share files with other users and even collaborate with them without worrying about unauthorized access. It uses a combination of security strategies like single sign-on, security threat alerts, view-only sharing and access, key management services, and CASB to safeguard your files during transit and at rest.
Client Portal
ShareFile is SaaS-based and can be accessed through a web-based UI from any device with an Internet connection. It even offers a mobile app for remote workers and people who are always on the go. On this portal, you can view workflows, get feedback and approval for file shares, and even track usage.
Overall, ShareFile offers a ton of security features to protect your sensitive data, thereby helping you comply with privacy regulations.
Pros:
- Easy to upload and share files.
- Automates notifications.
- Saves email addresses for repetitive use.
- Advanced cybersecurity features.
Cons:
- Limited templates for saving file-sharing settings.
- Limited integrations.
3. Tresorit
Tresorit is an advanced collaboration tool that offers efficient file sharing and document signing while preserving the security and integrity of your files and their content. It also maintains compliance and data control throughout the lifecycle of a document.
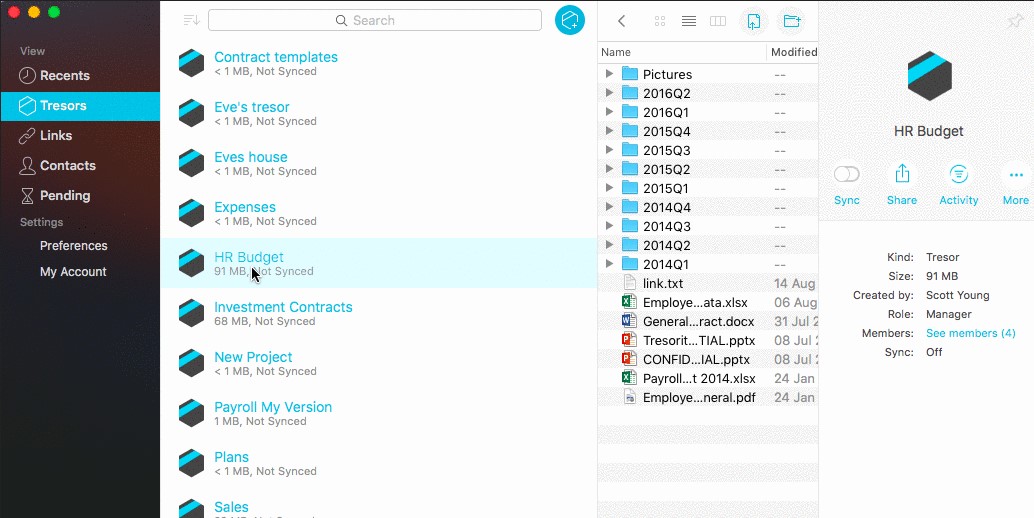
Source: Tresorit
Let’s now explore Tresorit’s features that help your organization stay compliant with regulations.
Encryption
Encryption is a central feature of Tresorit, as it offers security during file transfer and collaborations. A unique aspect of Tresorit is that it doesn’t store both the files and keys in the same environment. This way, even if an unauthorized user gains access to a network or system, your data is safe. Moreover, its encrypted data vaults add to your data’s protection.
Zero-knowledge Trust
Tresorit is based on a unique concept called zero-knowledge trust. What this essentially means is that no one can access your passwords or files – not even the employees of Tresorit. Such an approach ensures 100% security for your files. However, note that if you forget the master password, you can lose access to the file as no one else can access it.
Granular Settings
Tresorit offers many configuration options and settings to ensure the safety of your files. You can choose to watermark your documents to prevent unauthorized copying, create secure links for easy sharing, mandate an email ID to view the files, track who has viewed or modified files, and so much more. Such granular settings put you in complete control of the sharing process.
In all, Tresorit’s encrypted email and secure file transfer options help your company comply with regulations like GDPR, HIPAA, CSA, CCPA, and more.
Pros:
- Easy to store, share, and access files.
- Good customer support.
- Works well on Windows, Mac, and Linux.
- Advanced encryption.
Cons:
- Limited integrations.
- No support for macOS tagging.
4. NordLocker
NordLocker is a secure file-sharing service that protects your data when they are stored in the cloud or shared with others. Also, it ensures that all files are synced, backed up, and encrypted to prevent unauthorized viewing.
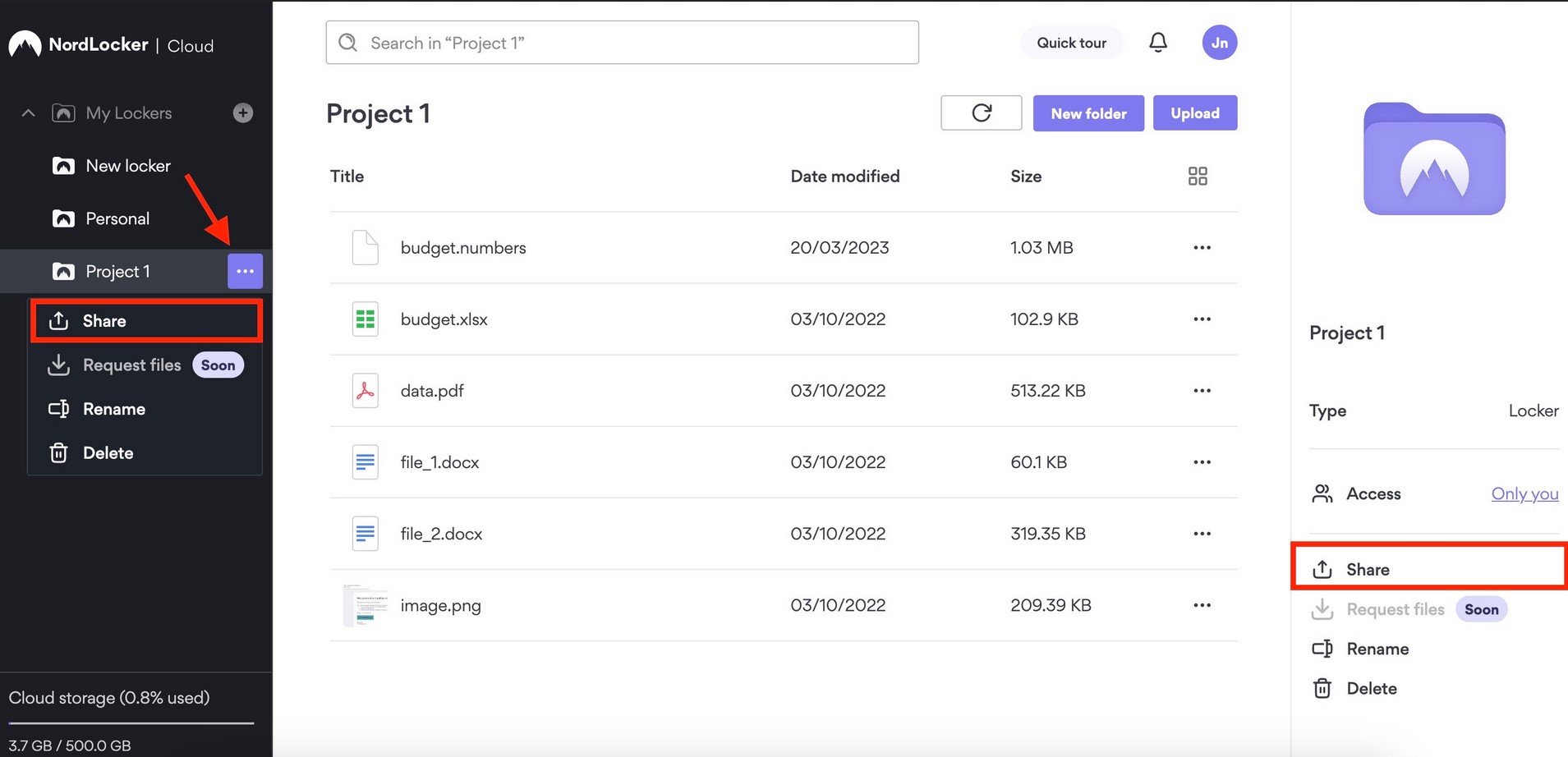
Source: NordLocker
Below are NordLocker’s features that help with maintaining security and managing compliance.
Easy to Use
A salient aspect of NordLocker is its ease of use. Using this tool, you can simply drag and drop files from any device, and they are automatically stored in the cloud. Every file that you add to the app is encrypted, and NordLocker supports all file formats, including documents, folders, images, and more. You can even organize files into folders and lockers, and store them on the cloud or locally.
Sync and Share
NordLocker works well across Windows, macOS, Android, and iOS devices, so you can seamlessly sync files between these devices. You can also access this tool through a web-based GUI without downloading the app. When you want to share, simply create a secure link and share it with others.
Encryption
On NordLocker, your files are always encrypted, and this means no one can access your documents without your permission. Also, it uses end-to-end encryption to secure and sync your files across devices. Above everything, there are no encryption limits.
Overall, NordLocker is a secure option to store and share your files. Its security features enable your organization to protect users’ data, resulting in compliance with regulations.
Pros:
- Supports multi-factor authentication.
- Easy to use
- End-to-end encryption.
- No restrictions on file size or format.
Cons:
- No apps for Linux
- File sharing with other NordLocker users only.
5. IBM Sterling Secure File Transfer
IBM Sterling is a unified file transfer platform that secures the files you transfer to your organization’s stakeholders. You can even track the sensitive files, who opened them and when, and other activities performed on their contents. More importantly, you can confidently meet your SLAs and comply with data regulations.
Source: IBM
Read on to learn IBM Sterling’s secure file transfer features.
Complete Visibility
You can use IBM Sterling to gain end-to-end visibility on all file activities. With its streamlined governance, you can quickly detect faults and meet your SLAs. Furthermore, you gain visibility into file transfers and B2B processes across your infrastructure. Also, you can define user roles, their security, and permissible actions to safeguard your files.
Scalable, Reliable, and Available
The event-based architecture of IBM Sterling ensures that you can easily scale up your file transfers to meet the needs of your growing business. There are no limits on file numbers or volumes. Its architecture is highly available, enabling you to consistently meet your SLAs. Also, this platform’s self-service capabilities and proactive alerts ensure its availability.
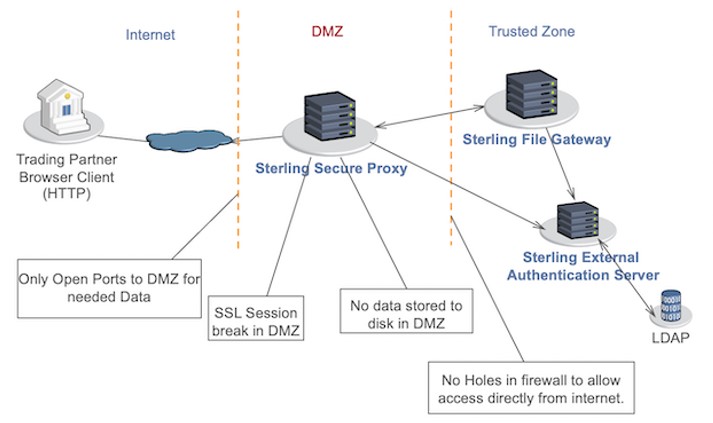
Advanced Security
IBM Sterling uses a DMZ-based proxy which prevents direct communication between internal and external sessions. Moreover, it supports firewalls, encryption, and other authentication mechanisms to ensure compliance.
In all, IBM Sterling is a proactive tool for meeting the compliance requirements of file transfers.
Pros:
- Configurable to meet your specific needs.
- Robust security.
- Extensive support for multiple protocols.
- Advanced automation.
Cons:
- More suited for large enterprises.
- The initial setup is complex.
Overall, these are the best secure file transfer software that protects your data, provides visibility, and helps meet regulatory requirements.
Final Words
In today’s business environment, remote work and collaboration are the operational cornerstones. At the same time, cyberattacks are growing. To strike a balance between collaboration and security, you need secure file transfer tools that will protect your sensitive data without compromising on collaboration or productivity. More importantly, these tools can help you comply with stringent data privacy and security regulations.
In this guide, we look at the different protocols of secure file transfers and a list of tools that combine cyber protection, ease of use, and compliance.